How to Use SSH Keys
Posted by Dave Eddy on Sep 20 2010What are ssh keys?
SSH keys are used for a user to authenticate over ssh without using the standard username/password combination. Because of the nature of the cryptography used, they allow a user to login without entering a password.
An ssh key is a type of public-key cryptography, with a public and private key-pair. The private key is, like its name says, meant to be kept private. When you make a private key, you should hold onto this private key and keep it secure; it is what is used for you to prove you are who you say you are. You can think of it like your password saved in a file. It is NOT actually your password stored in a file, but I compare the two because the file should be safeguarded with the same care as your passwords.
The public key can be published, it does not need to be kept secure. The public key allows people to encrypt data, but not decrypt it. In order to decrypt the data the private key is needed, that’s why it is important to keep it secure. The private key is kept on your client computer, and the public key is kept on your remote server, that will allow you to ssh from your client to your server using the ssh key.
How to create a key-pair
To create an ssh key-pair you must run the following command on your client computer (the computer that you will be ssh’ing from).
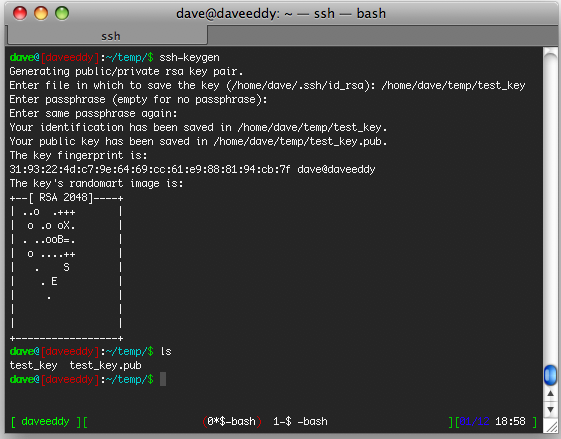
ssh-keygen
The command will ask you some questions, the first question is where you would like to save the ssh key-pair.
If you leave it blank it will default to ~/.ssh/id_rsa.
The next question will ask for a passphrase, if you don’t want ssh to ask for a password, leave this field blank and press enter (twice, it will ask you to confirm your passphrase). This passphrase will be used to encrypt the contents of the private key itself.
Generating public/private rsa key pair.
Enter file in which to save the key (/home/dave/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/dave/.ssh/id_rsa.
Your public key has been saved in /home/dave/.ssh/id_rsa.
The key fingerprint is:
19:c1:a2:79:e5:e6:c4:b9:c3:96:43:8a:bc:15:74:3e dave@puertorico
The command will then tell you that it has created two files, id_rsa which is the private key, and id_rsa.pub,
which is the public key.
How to use ssh keys
Now that you have a private and a public key generated, it’s time to transfer the public key onto your server. To transfer the key run this command.
scp ~/.ssh/id_rsa.pub username@server:~/.ssh/
Now that it is on your server you must move it to the correct spot.
ssh username@server
cd .ssh
cat id_rsa.pub >> authorized_keys
rm id_rsa.pub
The first thing you do is ssh into the server (which will require you enter your password, hopefully for the last time)! Then you go into the ~/.ssh directory, append the contents of the public key into authorized_keys, and remove the original public key file. The reason it is appended to authorized_keys is because you can have multiple public keys on one server inside that file.
All done
Now that the public key is on the server in the proper place, you can ssh into the server without having to enter a password! The only limitation is that you can only ssh in as the user who has the public key in their ~/.ssh directory (much like you can only ssh into a computer for users you know the password of).